The powershell history we were looking for
The powershell history we were looking for
Recently, I discovered a new way to obtain PowerShell history in Windows. While the location of the Bash history file is widely known, the file that stores PowerShell history is not as well-documented.
To gather accurate information about PowerShell history and the PSReadLine module, we can refer to Microsoft's official documentation. As far as I know, the PowerShell history file is mentioned in the following three articles:
- about_history (link)
- about_PSReadLine (link)
- Get-History (link)
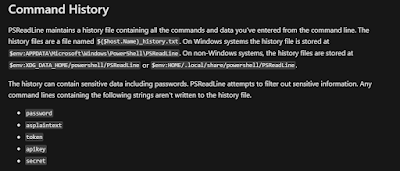
Some informations about where and how the history is stored
The Get-History cmdlet retrieves all commands executed in the current session. However, the PowerShell history file contains a persistent record of all commands executed by the user via PowerShell in clear text. This file is generated and maintained by the PSReadLine module, which is installed and enabled by default.
Whether you are a red teamer or a blue teamer, knowing how to access this file can enhance your workflow and investigative capabilities.
Retrieving the PowerShell History File Location Persistently
To locate and access the PowerShell history file, you can use the following methods:
1.Retriving the path of the file that sotres the powershell historyBy leveraging this knowledge, you can gain insights into past command executions, aiding in forensic analysis, security assessments, and automation improvements. Please notice how i was able to retrive passwords in clear-text too.
**This Article is only for Informational/Educational porpouse**






Commenti
Posta un commento