Case of Study : Hide PowerUp.ps1 from MS Defender
Hide PowerUp.ps1 from MS Defender
PowerUp.ps1 is a well-known script among pentesters for escalating local privileges. However, since it is fairly old and quite popular, Microsoft Defender detects it as malicious. To use it, we need to either create a custom version of the script or obfuscate the one available online.
In this guide, we will use a minimal obfuscation approach. By making small changes to the script, we can bypass Microsoft Defender’s detection and use the script without any issues.
What We need
- A Windows VM with the AV Signatures Updated
- The PowerUp.ps1 Script (here)
- The Tool DefenderCheck made by matterpreter (here)
- Notepad
Let's Start
The first step is to disable Microsoft Defender temporarily so we can download the PowerUp.ps1 script without interference.
After disabling Windows Defender, go to the GitHub page that contains the raw version of PowerUp.ps1. Copy the content and save it in Notepad with a .ps1 extension.
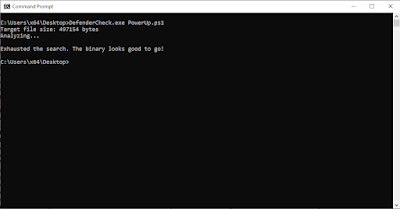
Once you have downloaded both the PowerUp script and the DefenderCheck tool, use DefenderCheck to identify the signatures that Microsoft Defender flags as malicious.
1st Signature
+ operator.2nd Signature
+ operator.+ operator.The file is clean (For MS Defender)













Commenti
Posta un commento